I just noticed that the fix for the hibernation problems that I was experiencing and had to contact Microsoft Product Support Services for is now available for download to those "customers running genuine Microsoft Windows".
The problem is detailed in Knowledge Base article 909095, The computer occasionally does not hibernate and you receive an "Insufficient System Resources Exist to Complete the API" error message in Windows XP with Service Pack 2, in Windows XP Tablet PC Edition 2005, or in Windows XP Media Center Edition 2005, and the fix is available here. One must validate Windows prior to downloading.
2006-08-31
Hibernation Fix is now available from Microsoft
2006-08-29
Oddities with Process Explorer / Detours / Packed Images
Sysinternals' Process Explorer can detect binary images it suspects are packed, and highlights them. Packed executables are highlighted in the top pane, and packed DLLs in a selected process are highlighted in the lower pane's "DLL View".
Interestingly, debug builds of binaries that link with Detours cause Process Explorer to suspect that the binary is packed ("Image is probably packed"). Release builds are not, however.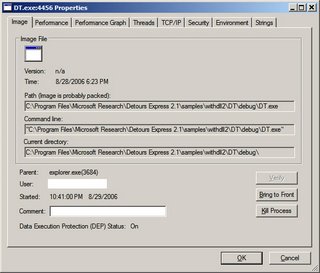
I would be interested to know how Process Explorer determines that a binary is probably packed.
2006-08-28
HTTP Irony
I had a bit of a chuckle this morning when I fired up SharpReader:
The feed for Eric Lawrence's InsideHTTP was bad because "the server committed an HTTP protocol violation".
2006-08-27
Poor Code Formatting with Blogger
In reviewing my previous post, "Initial Experience with Detours from Microsoft Research", I must say that I am not impressed with the way the code was formatted. Blogger ate up all of the nbsp's that I had put in. When I put them back in, Blogger chewed them up again.
Anyone know of a way to get source code to keep its formatting when posting? Hope I'm not missing something overly simple! <g>
Or is there simply a better way to do it? Thoughts / suggestions welcomed!
Initial Experience with Detours from Microsoft Research
Previously, I had been considering techniques that would allow me to RDP into a system and still be able to use my U3 Flash drive. I didn't want to have to log into a session on the glass, and then plug in the password for the U3 Launch Pad program. I want to plug the drive into the system in my office, and be able to hit it when I want to. I'm lazy.
Ultimately, I chose to explore Detours from Microsoft Research to accomplish this. I'm happy to report a rather simple, if somewhat unelegant, success. I simply downloaded Detours Express 2.1, explored the documentation a bit, and played with the samples. In under 2 hours, I had accomplished what I had set out to do - essentially make ProcessIdToSessionId return the same thing as WTSGetActiveConsoleSessionId.
Two of the Detours samples ("WithDll" and "Simple") were used in my solution. WithDll was just what I needed to jumpstart the LaunchU3.exe process with the code I wanted to "inject" into the process, so I was able to use that sample with absolutely no modifications.
The "Simple" sample provided framework code that I simply adapted to do what I wanted. Again, I was looking to "replace" ProcessIdToSessionId's implementation with:
*pSessionId = WTSGetActiveConsoleSessionId();
The code at the bottom of this post uses Detours to help me do just that. The code was written in Visual Studio 2005 / VC++ 8.0, so some of the CRT functions are the "Secure (_s)" versions. I didn't go through and do the _CRT_INSECURE_DEPRECATE #ifdefs.
So anyway, this works great, but normally the LaunchU3.exe program runs automatically when the USB drive is plugged into a system - a small partition presents itself as a read-only drive formatted with the CDFS filesystem. That partition contains an AutoRun.inf instructing Windows to kick off LaunchU3.exe. But I need to run WithDll.exe from the Detours Express package, not LaunchU3.exe.
Sounded like a killer application for an image file hijack ala "Image File Execution Options: Good, Evil, Fun":
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LaunchU3.exe\Debugger = "<path to>\WithDll.exe /d:<path to>\MyDetoursDll.dll "
Note the space before the closing quote of the value - the Debugger gets passed the image name, so the command to WithDll.exe looks like:
<path to>\WithDll.exe /d:<path to>\MyDetoursDll.dll x:\LaunchU3.exe
The only problem is that we do actually want to launch the specified program (LaunchU3.exe). But running LaunchU3.exe will kick off WithDll.exe, which will start LaunchU3.exe, which will start WithDll.exe... There are a couple of options to deal with this. The easiest is to copy LaunchU3.exe from the USB drive onto the hard drive and give it a new name - this was the approach that I took. Then, specify the following as the Debugger command in Image File Execution Options:
<path to>\WithDll.exe /d:<path to>\MyDetoursDll.dll <path to>\MyLaunchU3.exe
Another way would be to turn WithDll into a debugger - change the flags that get passed to the Detours function "DetourCreateProcessWithDll" to specify "DEBUG_ONLY_THIS_PROCESS", and incorporate a dummy debugger loop into the application, something like:
DEBUG_EVENT de = {0};
for( ;; )
{
WaitForDebugEvent( &de, INFINITE );
if( EXIT_PROCESS_DEBUG_EVENT == de.dwDebugEventCode ) break;
ContinueDebugEvent( de.dwProcessId, de.dwThreadId, DBG_CONTINUE );
}
When a process calls CreateProcess with DEBUG_PROCESS or DEBUG_ONLY_THIS_PROCESS specified in dwCreationFlags, the Debugger value of Image File Execution Options is not checked (makes sense, right? That's what the "Debugger" value is for). Thus, WithDll.exe can launch LaunchU3.exe without having LaunchU3.exe launch another instance of WithDll.exe. Launcherrific.
The last option is to modify the contents of the small CDFS partition on the U3 drive. This would allow one to toss the Detours programs (WithDll.exe and dependencies, as well as the "payload" DLL - a modified "Simple.dll" in this case) right onto the USB drive. Modify AutoRun.inf to kick off WithDll.exe with the right parameters, and the solution is clean and self-contained. Perhaps I will experiment with this... When I get more time =8->
Code for the Detours payload DLL:
#ifndef _WIN32_WINNT
#define _WIN32_WINNT 0x0501 // for WTSGetActiveConsoleSessionId
#endif
#include <stdio.h>
#include <windows.h>
#include "detours.h"
static BOOL (WINAPI* TrueProcessIdToSessionId)
( DWORD dwProcessId, DWORD* pSessionId ) = ProcessIdToSessionId;
static const unsigned short c_usLogTimeBufLen = 40;
static const unsigned short c_usMsgBufLen = 980;
static const unsigned short c_usFullMsgBufLen =
c_usLogTimeBufLen + c_usMsgBufLen;
static const char* const c_pszModName = "U3Detours";
void DebugPrint( const char* const pszFormat, ... )
{
char szNowTime[c_usLogTimeBufLen + 1] = {0};
SYSTEMTIME st = {0};
::GetLocalTime( &st );
_snprintf_s( szNowTime, c_usLogTimeBufLen, c_usLogTimeBufLen,
"%04d-%02d-%02d %02d:%02d:%02d.%03d", st.wYear, st.wMonth,
st.wDay, st.wHour, st.wMinute, st.wSecond, st.wMilliseconds );
va_list args;
va_start( args, pszFormat );
char szMsg[c_usMsgBufLen + 1] = {0};
_vsnprintf_s( szMsg, c_usMsgBufLen, c_usMsgBufLen, pszFormat, args );
va_end( args );
char szFullMsg[c_usFullMsgBufLen + 1] = {0};
_snprintf_s( szFullMsg, c_usFullMsgBufLen, c_usFullMsgBufLen,
"%s ==> %s(TID=%d): %s\n", szNowTime, c_pszModName,
GetCurrentThreadId(), szMsg );
OutputDebugString( szFullMsg );
}
BOOL WINAPI InterceptProcessIdToSessionId( DWORD dwProcessId,
DWORD* pSessionId )
{
BOOL bSuccess = TrueProcessIdToSessionId( dwProcessId, pSessionId );
if( !bSuccess )
{
DebugPrint( "ProcessIdToSessionId for PID %d failed with %d",
dwProcessId, GetLastError() );
}
else
{
DWORD dwActiveConsoleSessionId = WTSGetActiveConsoleSessionId();
DebugPrint( "ProcessIdToSessionId for PID %d succeeded; "
"SessionId %d intercepted and being set to %d",
dwProcessId, *pSessionId, dwActiveConsoleSessionId );
// This is all we're really looking to do...
*pSessionId = dwActiveConsoleSessionId;
}
return bSuccess;
}
BOOL APIENTRY DllMain( HMODULE hMod,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
(void)hMod;
(void)lpReserved;
LONG lErr = 0;
if( DLL_PROCESS_ATTACH == ul_reason_for_call )
{
DebugPrint( "Starting..." );
DetourRestoreAfterWith();
DetourTransactionBegin();
DetourUpdateThread( GetCurrentThread() );
DetourAttach( &(PVOID&)TrueProcessIdToSessionId,
InterceptProcessIdToSessionId );
lErr = DetourTransactionCommit();
if( NO_ERROR == lErr )
{
char szExe[MAX_PATH + 1] = {0};
GetModuleFileName( NULL, szExe, MAX_PATH );
DebugPrint( "Detoured ProcessIdToSessionId in PID %d(%s)",
GetCurrentProcessId(), szExe );
}
else
{
DebugPrint( "Error detouring ProcessIdToSessionId: %d", lErr );
}
}
else if( DLL_PROCESS_DETACH == ul_reason_for_call )
{
DetourTransactionBegin();
DetourUpdateThread(GetCurrentThread());
DetourDetach( &(PVOID&)TrueProcessIdToSessionId,
InterceptProcessIdToSessionId );
lErr = DetourTransactionCommit();
DebugPrint( "Removed ProcessIdToSessionId: %d", lErr );
}
return TRUE;
}
2006-08-26
Interrupts Abound!
I was having significant performance problems on a Windows XP SP2 laptop - the system was performing at 25% - 50% of its regular ability. So I pushed the "Turbo" button on the front, and that took care of everything.
In 1994, maybe.
No such fix for my problem. It was getting rather unbearable. I wanted to point the finger at Norton / Symantec software, but I didn't have hours to spend uninstalling it so I had to endure. I noted that the performance degradation came into play when there was moderate to heavy disk I/O.
Finally, I had some time to troubleshoot the problem. Process Explorer was telling me that Interrupts were monopolizing the CPU - 75% - 80% at times! I hadn't installed any hardware recently, and it was happening when the laptop was docked and undocked. Event Viewer didn't have any pertinent information.
After some thought, I recalled my observation about the performance degradation coinciding with disk I/O. I suspected that somehow the IDE channel had been set to PIO mode rather than Ultra DMA Mode 5. Device Manager confirmed my suspicions. Something (Windows?) had modified the setting for the Primary IDE Channel without notifying me. I uninstalled the primary IDE channel, rebooted, and let Windows redetect the hardware. The setting was back to Ultra DMA Mode 5, and the system was back to performing as it should have.
Microsoft Knowledge Base article "IDE ATA and ATAPI disks use PIO mode after multiple time-out or CRC errors occur" may provide some insight into how the transfer mode setting on my system was changed, but I'm running SP2 from August 2004 with all updates, and ATAPI.SYS referenced in the KB article is from April 2003. And, there was nothing in Event Viewer from ATAPI indicating that there were time-out or CRC errors.
2006-08-23
How does this warrant a KB article?
Found the following Microsoft Knowledge Base article today:
You receive an error message when you try to send an e-mail message by using the System.Web.Mail namespace in the .NET Framework 1.0
The gist of the article is that one should not use:
SmtpMail.SmtpServer.Insert(0, "mail.mycompany.com");
to change the Smtp.SmtpServer property. Rather, one should use:
SmtpMail.SmtpServer = "mail.mycompany.com";
Really? I'll make a note.
Further, the CAUSE section is kind of bogus - it states:
This issue occurs because the String.Insert method does not change the value of the SmtpMail.SmtpServer property. Therefore, the value of the SmtpMail.SmtpServer property is null.Now, my take on this is that the chances are pretty good that if a person is using the "problematic" method of setting SmtpServer, they might want to know WHY it is that "the String.Insert method does not change the value of the SmtpMail.SmtpServer property". (The answer, of course, is that String.Insert returns "a new String equivalent to this instance but with value inserted at position startIndex.")
At least the suggested resolution wasn't:
SmtpMail.SmtpServer = SmtpMail.SmtpServer.Insert(0, "mail.mycompany.com");
This type of problem, sadly, is probably rather common. I imagine that this type of thing happens all over the place. So why does this specific instance warrant a new article in the Microsoft knowledge base? I hope it doesn't mean that a bug resulting from the code depicted in 922777 was discovered in a Microsoft product...
Another possible fix for error 0x8ddd0009 with Windows Update / Microsoft Update?
[Added 2006-10-15: Another potential fix here...]
[Added 2006-09-19: Additional things to try here...]
[See other posts about 0x8ddd0009 here and here.]
Microsoft just posted knowledge base article 924092 today - "You experience problems when you use a Microsoft update service".
The CAUSE section states:
These problems may occur because some of the Windows Update Agent 2.0 files are missing or corrupted. Windows Update Agent 2.0 is required to use these products and services.This could be another way to fix the mysterious 0x8ddd0009 Windows Update / Microsoft Update error - intall the "Windows Update Agent 2.0" package.
2006-08-22
Some Updates - Protecting against Pointer Subterfuge and Kernel Patch Protection (PatchGuard)
1) Wrote a while back about "Protecting aginst Pointer Subterfuge". Michael Howard has updated the description of the algorithm used to encode pointers with EncodePointer/EncodeSystemPointer.
2) Previously, I pointed to an article on the Microsoft Driver site that details x64 Kernel Patch Protection. The Windows Vista Security blog has a higher-level description of kernel patching as well as some suggestions for alternatives.
2006-08-21
Windows Vista: You didn't actually want to INSTALL me, did you?
Windows Vista hates me. I've been wasting my time trying to get Vista beta 2 installed. I know, I know - "beta 2? That was released months ago!" But I've simply been too busy to install it even though I downloaded it when Microsoft opened up the Consumer Preview Program.
My first attempt at installing Vista was on a brand new hard drive. No partitions on it, no nothing. I booted the DVD I had burned the ISO to, and was greeted with a screen that looked like this:
Over and over and over and over again. The progress bar would complete, and the system would reboot, boot from the DVD, and go through the progress bar again. And again. And again. Ad nauseam.
I suspected a bad burn so I burned another disc. Same result. I ultimately tried 7 discs (DVD-R, DVD+R, DVD-RW) using 3 different software packages and 3 different burners (no rhyme or reason to my selection process). Always had the same result.
I googled a bit and discovered that I wasn't the only one with the problem where "Windows is loading files..." would display on the screen with a progress bar and setup would reboot after the progress bar completed... and the problems were most often related to a bad burn or a a bad download. Sigh.
After making 2 backups, I tried upgrading XP Pro to beta 2, using one of the same discs. Setup begain, and I was prompted for some information. When the file copy process began, I left to go do some other things. Coming back to the system, I was greeted with an error:
An error occurred while copying setup files onto your local machine. Error code is 0x80070241.I obtained access to another Vista beta 2 ISO image, burned it, and tried installing Vista. This time, the "Windows is loading files" screen looked a bit different - the font was different and there was a flashing white cursor at the end of the line with the progress bar:

I thought that was a bit strange. Once the progress bar completed, I was presented with an error message:
File: \windows\system32\winload.exe
Status: 0xc0000001
Info: The selected entry could not be loaded because the application is missing or corrupt
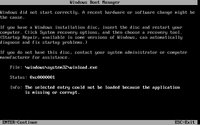
Once again, I tried buring with different media types, using different software and different hardware. Same results each time.
I was trying to avoid using a VM to run Vista because I actually wanted to get some real-world, day-to-day experience with it. But at this point I broke out VMware and mounted the ISO. The virtual machine did the same thing as the "real" machine - the same error messages and problems with the ISO images.
Looks like I'll have to wait until RC1 is released (hopefully sometime in early September) before I get a chance to install Vista...
2006-08-18
2006-08-17
VMware Player plays Virtual PCs
I had an interesting need the other day. I wanted to set up a test Windows Server 2003 box on a development system. I didn't have a license for VMware workstation that I could use on the development system, and I didn't want to install the free VMware Server since I've not yet had an opportunity to use it yet and this wasn't the time to start. VMware Player can only "play" (not create) virtual machines.
Virtual PC 2004 w/SP1 from Microsoft is now free. But I find that I prefer VMware's products to the Microsoft offerings. Not wanting to spend much time debating which virtualization package I should use, I went ahead and installed Virtual PC 2004 w/SP1. Whilst installing Windows Server 2003 Standard Edition into a virtual machine, I started wondering if VMware Player could interpret Virtual PC virtual machines.
The VMware Player product page states:
VMware Player also supports Microsoft virtual machines...It wasn't a large jump to interpret "Microsoft virtual machines" as "Virtual PC 2004 virtual machines". Indeed, that is the case. I finished installing Windows Server 2003 in Virtual PC 2004, and powered the VM off just after the final reboot that takes place during installation. I installed VMware Player, ran it, opened the Virtual PC 2004 .VMC file, and after a short import process I was able to start the virtual machine that I had created with Virtual PC 2004, in VMware Player.
So, for $0 (well, a Windows OS license is required) I was able to create a Windows Server 2003 virtual machine with Virtual PC 2004 and use it with VMware Player. Pretty cool...
2006-08-16
Error 0x8ddd0009 with Microsoft Update / Windows Update - What's Going On?
[Added 2006-10-15: Another potential fix here...]
[Added 2006-09-19: Additional things to try here...]
[See other posts about 0x8ddd0009 here and here.]
It seems that a LOT of people are getting error 0x8ddd0009 with Microsoft Update or Windows Update, and are looking for fixes to the problem.
Previously, I had noted that I had gotten around the problem by correcting the system time on the affected computer. But apparently that's not the only "fix" for the problem. Given that it doesn't do the trick for everyone, here is a compilation of suggestions that I have run across. Note that I haven't tried all of them and I can't vouch for their accuracy. Some suggestions involve the use of a 3rd party program or utility. Use them at your own risk.
If you have gotten the 0x8ddd0009 error from Microsoft Update or Windows Update and something listed here fixes it, please chime in. Also, if you did something not listed here and it took care of the problem, please share your resolution with others.
I can't find any reference to 8ddd0009 OR 0x8ddd0009 in the Microsoft knowledge base, so we're pretty much going off of community references here.
While most of the people reporting 0x8ddd0009 seem to be running Windows 2000 with some recent service pack (3 or 4), some are running Windows XP SP2.
To restate, I fixed my problem by ensuring that the system time on the affected computer was accurate - it had been about 22 minutes off. Once I corrected the time, the problem went away.
Another thing to do is to make sure that the computer that is having problems has sufficient free space available on the disk. I'll grab 1 GB out of the air and toss it in here - make sure there's 1 GB of free space on the disk. Just to be safe...
Several people report that uninstalling Windows Installer 3.1 resolved the 0x8ddd0009 error. To uninstall Windows Installer 3.1, use the "Add or Remove Programs" applet in the Control Panel, and find "Windows Installer 3.1 (KB893803)" in the list, and click the "Remove" button. Alternatively, running "%WINDIR%\$MSI31Uninstall_KB893803v2$\spuninst\spuninst.exe" from Start --> Run may do the trick.
Running regsvr32 /u "%systemroot%\system32\mobsync.dll" has apparently worked for at least one individual; Microsoft Knowledge Base article "Event ID 4100 appears repeatedly in Event Viewer details this approach (not in the context of the 0x8ddd0009 error, though), and also the implications:
After you unregister Mobsync.dll, Client Side Caching (CSC) no longer works. The behavior described in the "Symptoms" section of this article does not affect CSC functionality, but unregistering Mobsync.dll doesIf that doesn't do the trick, one should be able to UNDO the unregistration (???) of Mobsync.dll by running regsvr32 "%systemroot%\system32\mobsync.dll". Might be worth a shot...
Other people report that downloading / installing / running a program called "Dial-A-Fix" (apparently free) and using it to fix "Windows Update" (whatever that program considers "Windows Update") fixes the problem. The program can likely be found here. And here are extensive instructions for using the program to fix the problem.
Re-running the "Connection Setup Wizard" (presumably, in IE's Tools --> Internet Options --> Connections tab --> "Setup..." button; it can also be run by tossing "rundll32.exe netshell.dll,StartNCW" in the Start --> Run box) is reported to have resolved the 0x8ddd0009 error for several people.
Another thing that has worked in certain cases is running regsvr32 msxml3.dll from the Start --> Run box or a Command Prompt.
Something else to try is to run the following commands from a Command Prompt (Start --> Run --> Cmd):
proxycfg -d
net stop wuauserv
net start wuauserv
Disabling any firewalls might be another thing to try.
Some have indicated that following the instructions in Microsoft Knowledge Base article Error messages that you may receive when you try to download and install updates from the Windows Update Web site, from the Microsoft Update Web site, or from a WSUS server: "0x800704DD," "0x80240020," or both took care of the 0x8ddd0009 error for them.
Stopping the "Automatic Updates" service (from the Services management console snap-in - Start --> Run --> Services.msc, or by running net stop wuauserv), and deleting (renaming is less destructive, I suppose) the %windir%\SoftwareDistribution folder can also resolve various issues with Microsoft Update / Windows Update.
On a more drastic note, uninstalling Windows XP Service Pack 2 and then reinstalling it took care of the 0x8ddd0009 error for at least one person.
Again, if you have gotten the 0x8ddd0009 error from Microsoft Update or Windows Update and something listed here fixes it, please chime in. Also, if you did something not listed here and it took care of the problem, please share your resolution here so that others may benefit.
2006-08-15
Virtualization, Applied to Wireless Networking
I've been using wireless networking for a couple of years now. I have a few wireless routers on my network, and often while troubleshooting various connectivity issues (is it related to the environment, or to the settings on the router, or is it a driver issue, or...) I've wished for the ability to connect to multiple wireless networks simultaneously. Without having to have a separate wireless card for each wireless network. Looks like Microsoft Research is working on a project that allows one to do just that.
The project is called "Virtual WiFi", and sounds pretty cool. The current implementation is a functional prototype and doesn't have certain features yet, but the basic functionality is there. WEP or 802.1x is not supported yet, and support for multiple cards has not been fully implemented (driver supports it, "user level code"/"VirtualWiFi service" does not).
A Virtual WiFi FAQ can be found here, and the Virtual WiFi software can be downloaded here.
Have to wonder a bit about the potential ramifications of this software on security - what happens when one connects the wireless card to an unsecured "public" network AND the corporate wireless network? I suppose, that's not much different than connecting to the wired corporate network and using the wireless card to connect to an unsecured public network...
2006-08-12
More on NTFS Alternate Data Streams (ADS)
With my recent antics involving NTFS Alternate Data Streams (ADS), I had an idea for an application. None of the tools I have used or heard of offered the ability to extract a stream from a file or folder and save it as a "stand-alone" file. Integrated viewing / inspection / editing of the streams ala "Fiddler" would also be quite cool. And of course, the ability to append a stream to a file or folder, or copy / move a stream from one "host" to another could come in handy in certain situations.
Strange it was then that I accidentally stumbled across a utility published recently by PC Magazine called Stream Revealer. Stream Revealer seems to have many of these features. It includes the ability to "View" streams in Text / Hex, the ability to extract streams, and the ability to attach a stream to a file. It also integrates with FileSnoop, another PC Magazine utiltity that allows one to "snoop" or preview the contents of a file.
I haven't used the utility as it costs $7.97 to download unless one has a PC Magazine "Utility Library" subscription. Still, if / when one needs the features described above, $7.97 is a heckuva lot cheaper than it would cost to develop the utility one's self...
2006-08-09
NTFS Alternate Data Streams
[2006-09-29: Related post here...] I was recently exposed to a "White Paper" (love the term...) called "Alternate Data Streams – What’s Hiding in Your Windows NTFS?" I was a bit disappointed as I was hoping to learn a bit more about alternate data streams. I really didn't pick up anything new, aside from the introduction of a few software utilities that can somewhat facilitate manipulation of ADS. A few things in the paper were left unexplored though. The paper states:
When you use Microsoft Internet Explorer (at least through version 6) to download and save files from the Internet, the browser creates an ADS called Zone.Identifier. This file contains information about the Internet zone from which the file was downloaded.We have yet to discover why we might need that information, but that is what it does.Without direcly stating that ADS is the underlying mechanism (it only states "The Web content zone information is saved together with the files only if the hard disk uses the NTFS file system"), Description of how the Attachment Manager works in Windows XP Service Pack 2 describes what the information in the ADS is used for. Further, this behavior is new with Windows XP Service Pack 2, and was not present in previous versions of IE ("at least through version 6"). The paper also states:
In the Windows XP Windows Explorer, if you choose the View –> Thumbnails option for pictures, it appears to create the thumbnail as an ADS. These files have names similar to {4c8cc155-6c1e-11d1-8e41-00c04fb9386d}. Very informative, as you can see. Note that we are not certain that this is the thumbnail, since we’ve yet to find a way to open one of those files. However, using the utilities discussed above, we can clearly see that choosing View –> Thumbnails creates ADSs behind picture files.I tried to do just what the author described, but I was unable to see any files OR streams named with the {xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx} convention. It's a GUID, of course - it's not meant to be informative - just unique. The statement about not being able to "find a way to open one of those files" is rather interesting. Try a binary editor or even a simple text editor like Notepad - what's in the stream? I decided to do a bit of digging, and found plenty of references to the GUID the author mentioned - {4c8cc155-6c1e-11d1-8e41-00c04fb9386d} - in fact, Googling the GUID (alliteration?) yields about 1000 results. That seemed like a lot of hits for a GUID that, based on the author's description, was a filename or stream name for a thumbnail. Turns out that running FileMon on my system and filtering for "4c8cc155" turns up a bunch of hits (er... misses?) when I start browsing the file system with Windows Explorer. Specifically, an attempt was made to open an ADS named {4c8cc155-6c1e-11d1-8e41-00c04fb9386d} on each folder I browsed to, and each file that I selected. So it would seem that something else is going on here. I wondered what the shell (explorer.exe) would do if it found such a stream on a folder or file, so I made one. Nothing significant happened. Then I tried simply changing the view of a folder (without the ADS {4c8cc155-6c1e-11d1-8e41-00c04fb9386d}) to "Thumbnails". FileMon indicated that explorer.exe tried to open the ADS in question on the folder. Nothing earth shattering here. Next, I created a test folder with a test file - molotov.eee. I did a "Properties" on the file, and hit the Summary tab. I entered some garbage in the Title and Subject fields, and hit "Apply". FileMon showed that explorer.exe indeed created a stream named {4c8cc155-6c1e-11d1-8e41-00c04fb9386d} on molotov.eee. It would appear that our mysterious GUID-named stream is related to the "Summary" metadata that one can specify for most / all files. Interestingly, tossing garbage in the {4c8cc155-6c1e-11d1-8e41-00c04fb9386d} stream causes Explorer to not display the Summary tab when one views the Properties of the subject file. It must not recognize the format, decide that the stream is used for something else, and in the interest of stability or not overwriting data chooses not to provide an interface to view the uninterpretable stream. A 0 byte stream named {4c8cc155-6c1e-11d1-8e41-00c04fb9386d} on a file does not have an impact on whether or not the shell chooses to display the Summary tab in the file's Properties. In fact, the stream that Explorer creates is 0 bytes. The real meat of the Summary information, then, must be in the other stream that's created - the ♣SummaryInformation stream - which does vary in size based on what is entered in the Summary fields.
2006-08-08
ASP.NET Signed assemblies in "BIN" directory not supported?
I ran across an article in the Microsoft knowledge base that really got me worrying: PRB: "Can not Access File 'AssemblyName' Because It Is Being Used by Another Process" Error Message in ASP.NET. The shocker is in the CAUSE section:
CAUSEWhat? Where is this documented (besides the KB article)? Why? And what versions of the .NET Framework does this apply to? The KB article states it applies to the .NET Framework 1.1 and 1.0 / ASP.NET 1.1 and 1.0, but the article's "Last Review" was on 2005-09-27 - before the .NET Framework 2.0 / ASP.NET 2.0 was officially released. Is the article simply waiting for an update? Another article that makes one wonder if the .NET Framework 2.0 / ASP.NET 2.0 is affected is PRB: "Access Denied" Error Messages When You Do Not Put Strong-Named Assemblies in the Global Assembly Cache. This article's "Last Review" was on 2004-01-24, but it states that it applies to "Microsoft Web Services Enhancements for Microsoft .NET 2.0". I'm probably being way too literal, but couldn't one at least glance at that and think it applies to the .NET Framework 2.0? Anyway, Tess Ferrandez writes in her blog "If broken it is, fix it you should":
This problem occurs because signed assemblies in the Bin directory are not supported.
...strong named assemblies, irrespectively of where they are loaded from are loaded into a shared domain (they are domain neutral)... ...Since the assemblies in the shared domain are not unloaded when the app domain unloads they may get locked if you are unlucky with timing. Locking issues most frequently occur with processes that frequently scan folders such as index server, virus scanning software or backup software... ...If a strong named assembly is used by multiple web applications and each application grants it varying permissions or if the permission grant varies between application domain restarts, you might see errors like “AssemblyThat would explain the "Why" (article 813833 makes a similar statement, but Tess goes into more detail). But it's not clear if the .NET Framework 2.0 / ASP.NET 2.0 is affected until you look at the comments, where Tess states:.dll security permission grant set is incompatible between appdomains”...
In 2.0 the assemblies are not loaded domain neutral [...] there was a very specific reason i mentioned 1.1. (and 1.0 for that matter)and
the issue is due to the dlls being loaded in the shared domain in 1.0 and 1.1. which no longer occurrs in 2.0 [...]An interesting comment to Tess' post points one to FxCop's AssembliesShouldHaveValidStrongNames rule. FxCop likes assemblies to be signed, but there's nothing that says they have to go in the GAC... Ouch.
2006-08-07
OS Loader Lock and mda:loaderLockMsg / CanRunManagedCode?
I have an annoying problem with Outlook 2003 crashing on me sometimes when I shut it down. Usually, if I'm closing Outlook, I'm leaving for the day. That means that I don't necessarily have the time nor the desire to try to figure out what's going on. I just clear the box that wants to restart Outlook, choose not to send the report to Microsoft (sorry!), and go on my merry way.
One day, I finally looked into things a bit. I chose to debug the problem, which kicked off VSJITDebugger.exe (Visual Studio Just-In-Time Debugger), and let me pick a new Visual Studio 2005 instance.
In the Output window of VS2005, I saw the following and tossed it into a "New Text Document":
<mda:msg xmlns:mda= "http://schemas.microsoft.com/CLR/2004/10/mda">
<!--
Attempting managed execution inside OS Loader lock. Do not attempt to run managed code inside a DllMain or image initialization function since doing so can cause the application to hang.
-->
<mda:loaderLockMsg break="true"/>
</mda:msg>
> mscorwks.dll!MdaXmlMessage::SendDebugEvent() + 0x1c8 bytes
mscorwks.dll!MdaXmlMessage::SendMessage() + 0xf3 bytes
mscorwks.dll!MdaXmlMessage::SendMessagef() + 0xa9 bytes
mscorwks.dll!MdaLoaderLock::ReportViolation() + 0x13d bytes
mscorwks.dll!CanRunManagedCode() + 0xa64de bytes
mscorwks.dll!Unknown_Release() + 0x18 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x1a02 bytes
[Frames below may be incorrect and/or missing, no symbols loaded for LookoutAddinShim.dll]
LookoutAddinShim.dll!DllGetClassObject() + 0x1974 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x2650 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x3dbb1 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x22033 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x21f67 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x1dd01 bytes
LookoutAddinShim.dll!DllGetClassObject() + 0x1df5f bytes
ntdll.dll!_LdrpCallInitRoutine@16() + 0x14 bytes
ntdll.dll!_LdrUnloadDll@4() + 0x7569 bytes
kernel32.dll!_FreeLibrary@4() + 0x19 bytes
ole32.dll!CClassCache::CDllPathEntry::CFinishObject::Finish() + 0x25 bytes
ole32.dll!CClassCache::CFinishComposite::Finish() + 0x1599e bytes
ole32.dll!CClassCache::CleanUpDllsForApartment() + 0x63 bytes
ole32.dll!FinishShutdown() + 0x64 bytes
ole32.dll!ApartmentUninitialize() + 0x51 bytes
ole32.dll!wCoUninitialize() + 0x3f bytes
ole32.dll!_CoUninitialize@0() + 0x52 bytes
OUTLLIB.DLL!DllCanUnloadNow() + 0x13062 bytes
OUTLLIB.DLL!RenExitInstance@0() + 0x204 bytes
kernel32.dll!_BaseProcessStart@4() + 0x23 bytes
And of course I had to get going by the time all of the symbols were loaded, etc, so I closed the debugger and left for the day. But the output above seems to point to Lookout doing something naughty inside of the OS loader lock. (A list of naughty things can be found in the documentation for DllMain and "DllMain Restrictions" in "Mixed DLL Loading Problem".) I assume the message above is the implementation of the "Proposed Long-Term Solution" described in "Mixed DLL Loading Problem":
In addition to providing the managed module initializer mechanism to fix the loader lock problem in newly compiled images, this solution also provides checks to prevent the common language runtime from executing unsafe images that may have been built with old tools.This would make sense, since LookoutAddinShim.dll is a mixed image - it is a COM component with dependencies on MSCOREE.DLL. In my case, it is using the .NET Framework 2.0, which presumably has incorporated the "Proposed Long-Term Solution" described in "Mixed DLL Loading Problem" as it certainly is "the next version of the common language runtime (after version 1.1)".
Generally, the "OS loader lock" issue is best dealt with by following the instructions specified in the Managed Extensions for C++ Reference at "Converting Managed Extensions for C++ Projects from Pure Intermediate Language to Mixed Mode".
I should note that I'm not sure what specifically caused Outlook to crash - the above is just a message that was in the Output window in Visual Studio 2005. It may or may not be the culprit.
2006-08-04
Signing the Enterprise Library for .NET Framework 2.0 - January 2006
So I've been messing with the Enterprise Library for .NET Framework 2.0 - January 2006 a bit lately (see also patterns & practices: Enterprise Library: Home). Since I'm using strong-named assemblies, I needed to sign the assemblies from the Enterprise Library in order to use them. It seems, however, that this scenario was given little thought since it is quite tedious to do this. Ultimately, through sheer brute force I did manage to get them signed using a key container rather than a key file. Here's how...
Use Windows' "Search" function to find *.csproj in the root installation folder for the Enterprise Library ("C:\Program Files\Microsoft Enterprise Library January 2006" by default) and all sub-folders. Select all of the files (102 of them), right-click, and choose "Properties". Click the box to clear the "Read-only" check box, and "OK" the changes.
Then, open Visual Studio 2005 and use the "Find In Files" feature to find files containing a space, of type *.csproj, in the root installation folder for the Enterprise Library (again, "C:\Program Files\Microsoft Enterprise Library January 2006" by default) and all sub-folders. Also tick the "Display file names only" box.
The names of the 102 files will display in the "Find Results 1" area. In each (EACH!) CSPROJ project file, add <KeyContainerName>ContainerName</KeyContainerName> to the first <PropertyGroup> section, as described in Signing Assemblies in Visual Studio 2005 with Key Containers . If I wouldn't have been so adept at the "click, paste, F8" trio (position the iBeam, paste the key container blurb, go to the next CSPROJ file), I probably would have automated the process with some code or something. Anyway, if this is all one does and one saves the files and then tries to build the Enterprise Library, one gets several CS1726 compiler errors.
Compiler Error CS1726 Error Message
Friend assembly reference 'reference' is invalid. Strong-name signed assemblies must specify a public key token in their InternalsVisibleTo declarations.
To get past the CS1726 errors, more details need to be added to the "InternalsVisibleTo" attribute for various assemblies - specifically, the public key. The public key can be obtained by starting a Visual Studio 2005 Command Prompt or SDK Command Prompt and using SN.EXE (the "Microsoft (R) .NET Framework Strong Name Utility") to extract the public key from the key container:
sn -pc ContainerName PubKeyFile
Then, SN.EXE is used again to display the public key:
sn -tp PubKeyFile
, PublicKey=002400000480000[...]559ea [truncated for brevity]
Copy that whole blurb to the clipboard. Next, use Windows' Search function to find all files named "AssemblyInfo.cs" in the root installation folder for the Enterprise Library and all sub-folders, containing the text "InternalsVisibleTo". Again, select all of the files (15 of them), right-click, and choose "Properties". Click the box to clear the "Read-only" check box, and "OK" the changes.
Then, bring up "Find In Files" in Visual Studio 2005 again, and search the root installation folder for the Enterprise Library for files named AssemblyInfo.cs containing "InternalsVisibleTo". Again, make sure the "Display file names only" box is checked. There should be 15 hits, but note that some files have more than one "InternalsVisibleTo" attribute. Place the iBeam in the attribute after the assembly name, and paste the public key. The attribute should change from something like:
[assembly: InternalsVisibleTo( "Microsoft.Practices.
EnterpriseLibrary.Caching.Tests" )]
to something like:
[assembly: InternalsVisibleTo( "Microsoft.Practices.EnterpriseLibrary.
Caching.Tests, PublicKey=002400000480000[...]559ea" )] [truncated for brevity]
Change all of the files, save the changes, and build the Enterprise Library. The library should now build successfully.
Note that you can use the "Build Enterprise Library" shortcut in the "Microsoft patterns & practices\Enterprise Library - January 2006" program group, but by default it builds a debug configuration. To build the release configuration, open a Visual Studio 2005 Command Prompt or SDK Command Prompt, navigate to the root installation folder for the Enterprise Library, and run BuildLibrary.bat specifying "Release":
BuildLibrary Release
Then, to copy the assemblies to the bin folder, run CopyAssemblies.bat, also specifying "Release":
CopyAssemblies Release
To copy the assemblies elsewhere, supply the location to CopyAssemblies.bat, like:
CopyAssemblies Release C:\EntLibJan2006
2006-08-03
Visual Studio 2005: Trivial Leftovers in AssemblyInfo.cs
I noted the following the other day when I was doing some C# development...
If one creates a new "Windows Application" and examines AssemblyInfo.cs, it has the following content:
// Version information for an assembly consists of the following four values:
//
// Major Version
// Minor Version
// Build Number
// Revision
//
[assembly: AssemblyVersion( "1.0.0.0" )]
[assembly: AssemblyFileVersion( "1.0.0.0" )]
However, if one creates a new "Class Library" and examines AssemblyInfo.cs, one sees the following:
// Version information for an assembly consists of the following four values:
//
// Major Version
// Minor Version
// Build Number
// Revision
//
// You can specify all the values or you can default the Revision and Build Numbers
// by using the '*' as shown below:
[assembly: AssemblyVersion( "1.0.0.0" )]
[assembly: AssemblyFileVersion( "1.0.0.0" )]
Of course, the '*' notation in the comments for the Class Library (in this case, at least) that incorrectly indicates the '*' is "shown below" is a remnant of Visual Studio .NET 2002 and Visual Studio .NET 2003, where the default for the AssemblyVersion attribute was a value like "1.0.*".
According to the AssemblyVersionAttribute Constructor on MSDN, specifying "1.0.*" sets the "build number" value to be equal to the number of days since January 1, 2000 local time, and "revision" to be equal to the number of seconds since midnight local time, divided by 2. Specifying "1.0.1.*" sets the "revision" to be equal to the number of seconds since midnight local time, divided by 2.
To remove the minor inaccuracy, one could probably change the inaccurate comment by modifying the project template at either %PROGRAMFILES%\Microsoft Visual Studio 8\Common7\IDE\ProjectTemplatesCache\CSharp\Windows\1033\ClassLibrary.zip\AssemblyInfo.cs, or AssemblyInfo.cs in %PROGRAMFILES%\Microsoft Visual Studio 8\Common7\IDE\ProjectTemplates\CSharp\Windows\1033\ClassLibrary.zip. Alternatively, one could change the values of AssemblyVersion and AssemblyFileVersion...»
2006-08-02
Signing Assemblies in Visual Studio 2005 with Key Containers
When signing an assembly, I prefer to use key containers rather than key files. Just specify a key name in AssemblyKeyName and the assembly is signed with that key provided that it has been installed on the machine. Installing the key into a key container is easy. Take the keyfile (keyfile.snk) obtained by running sn -k keyfile.snk from a Visual Studio / SDK Command Prompt and run it with sn -i keyfile.snk keycontainer. Set AssemblyKeyName in AssemblyInfo.cs to "keycontainer" ([assembly: AssemblyKeyName("keycontainer")]) and the assembly will be signed with the key in keycontainer.
At least, that's how it worked in Visual Studio .NET 2002 and Visual Studio .NET 2003. In Visual Studio 2005, if one uses the AssemblyKeyName attribute in AssemblyInfo.cs, one gets the following warning:
Properties\AssemblyInfo.cs(16,12): warning CS1699: Use command line option '/keycontainer' or appropriate project settings instead of 'AssemblyKeyName'
This is fine, except a reason we'll get into later. If one looks up C# compiler warning CS1699 in the VC# Reference, one will note that "Prior to Microsoft Visual C# 2005, you specified the key file using CLR attributes in source code. These attributes are now deprecated". The warning description goes on to list security, usability, and decreased compiler efficiency as reasons for the deprecation.
Now, the reference page for CS1699 also states "Beginning in Microsoft Visual C# 2005, you should use the Signing Page of the Project Designer or the Assembly Linker to specify the key". The problem here is that the "Signing Page" has no place to specify a key container!
CS1699's documentation points one to a page titled "/keycontainer (Specify Strong Name Key Container) (C# Compiler Options)". On that page one finds the following tasty morsel:
To set this compiler option in the Visual Studio development environment
Well, that would explain how this can lead to an increase in compiler efficiency!
You can't specify any additional options to the C# compiler via the IDE, and there's no way to specify a keycontainer on the "Signing Page".
Luckily, there is a way to specify a keycontainer without using the AssemblyKeyName attribute. One needs to close the C# project and open up the .csproj file for the particular project in an XML editor ("Notepad"). In the first <PropertyGroup> element one can add the following line, replaing [containername] with the name of the key container one wishes to use:
<KeyContainerName>[containername]</KeyContainerName>
Note that as tempting as it may be, you need to leave the value of the "SignAssembly" element as false. Apparently, "SignAssembly" really means "use an assembly key file".
Open up the project again and build the assembly, and it should be signed with the key that was installed into the container specified in the KeyContainerName.
»
2006-08-01
More fun with Community Solutions in the Microsoft Knowledge Base
See other "interesting" posts about Community Solutions articles here and here.
The "Welcome to the Terminal Services Community" page on Microsoft.com currently has a bunch of interesting links in the "Windows Server Solutions by MVPs" section:
»










